
Executive brief
SILQFi in Riyadh plans a Shariah compliant program for tokenized invoice finance. Helix is the partner. The design uses restricted transfers so only allow listed wallets can hold or move the tokens. As a result the issuer can control who buys, who sells, and when funds redeem. In short this is a tested credit idea with an on chain wrapper. No investment advice.
Key takeaways
First, the product targets approved invoices from known suppliers.
Second, tokens carry built in rules for transfers and redemptions.
Third, cash sits in custody with a licensed firm and reports arrive on a set schedule.
Finally, a Shariah board reviews the pool so that yield comes from trade and not from interest.
Why this matters
Saudi policy favors digital rails for small and mid size firms. Therefore a tokenized credit pool can speed working capital and improve data. Meanwhile investors gain program level disclosure that looks the same every month. In addition the allow list keeps the asset inside a known group. Together these traits make the idea attractive to regulated buyers.
How it works step by step
Step one. A supplier issues an invoice after a real delivery.
Step two. The invoice moves to a special purpose entity after a true sale.
Step three. The pool mints tokens that represent cash flow rights.
Step four. Only wallets on the allow list can buy or trade those tokens.
Step five. Cash from buyers sits with a licensed custodian.
Step six. When the buyer pays the invoice the program redeems tokens for cash.
Step seven. Reports show pool size, aging buckets, and realized yield.
What restricted means
Restricted means the token enforces rules. Transfers can pause during audits. Holding periods can apply during settlement. Only approved counterparties can receive the asset. Because rules live in the contract, checks run before each move. Consequently the issuer can respect local offering rules and Shariah screens.
Governance and custody blueprint
Legal wrapper. A special purpose entity holds the invoices after a true sale.
Shariah screening. An independent board reviews assets and fees on a fixed schedule.
Token logic. Allow listed transfers, pause switches, and clear redemption paths.
Custody. Segregated cash accounts with monthly reconciliation.
Oracles. Updates on invoice status, payment confirmation, and delinquency flags.
Reporting. Pool tapes with aging buckets and realized yield.
Insert PNG here lifecycle of a tokenized invoice from origination to redemption with the restricted transfer logic highlighted.
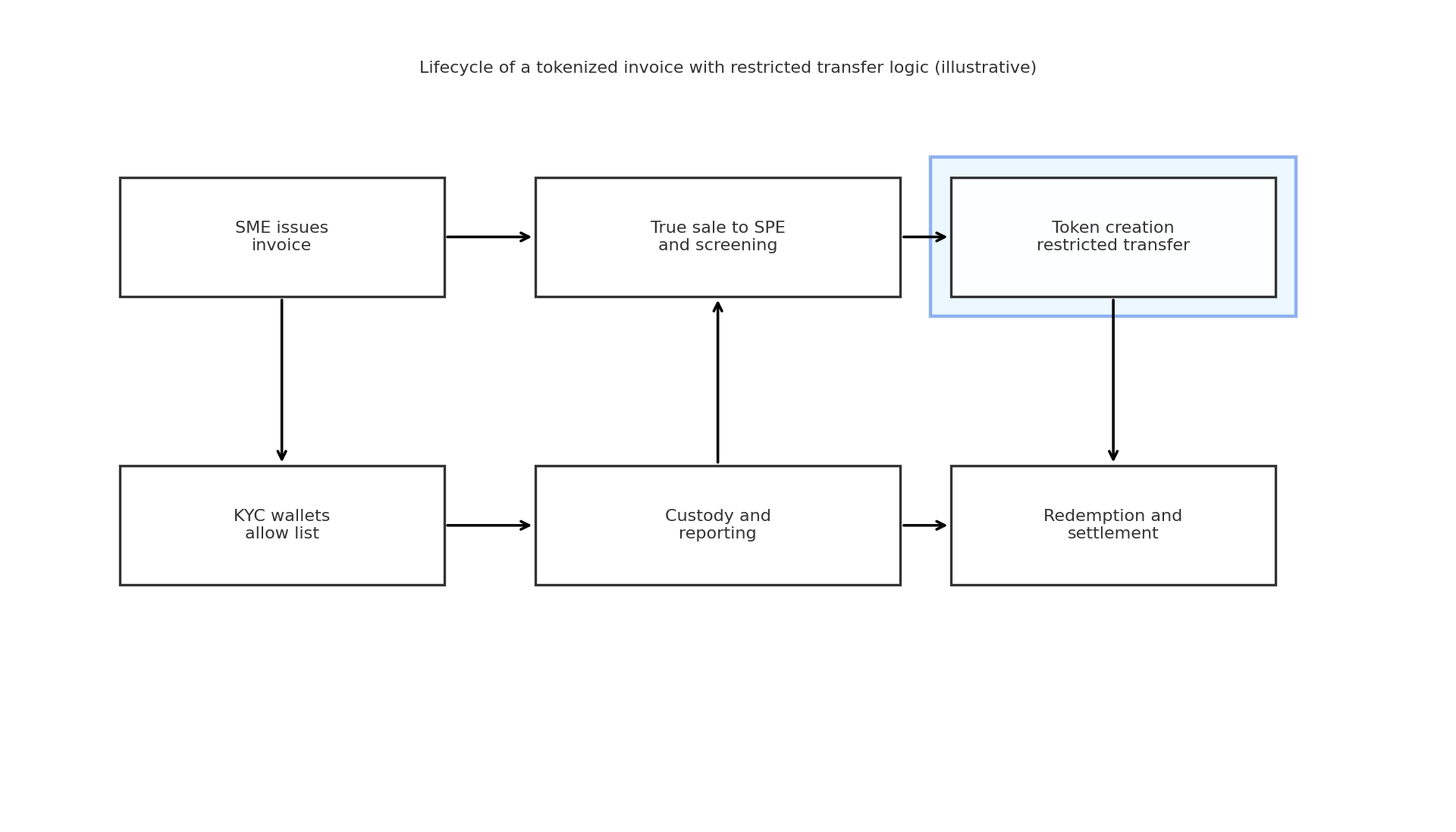
Figure 1. Diagram lifecycle of a tokenized invoice from origination to redemption
Risks and simple mitigations
| Risk | Why it matters | Practical mitigation |
|---|---|---|
| Legal enforceability | Token rights must match off chain claims | Clear assignment language and court recognition of digital records |
| Shariah drift | Yield engineering can hide interest like flows | Independent board and transparent fee tables |
| Data integrity | False invoices or late payments can hurt returns | Verified issuers, third party checks, and insurance where viable |
| Liquidity | Holders may need a way out before maturity | Staggered maturities and periodic redemption windows |
| Key person risk | Small teams raise execution risk | Operational redundancy and escrow of critical code |
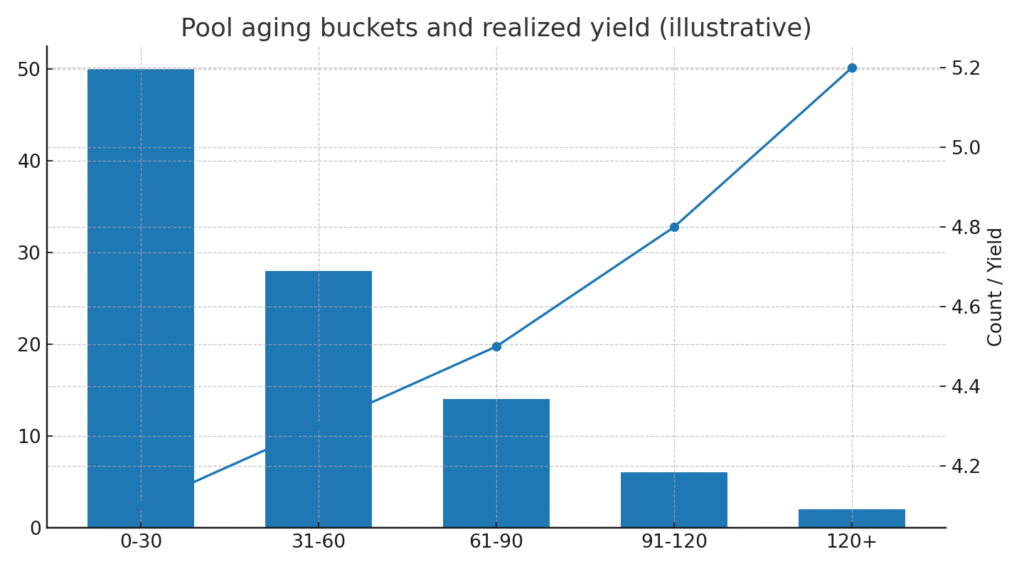
Figure 2. Chart pool level aging buckets and realized yield distribution
Use cases in the region
For suppliers the program can unlock cash against approved receivables. For banks it can free balance sheet while keeping oversight. For qualified investors it can add short duration yield with strong controls. Meanwhile regulators can track flows through standard reports. Therefore every party gains a clear view of risk.
What would convince institutions
First a full cycle of data that shows realized losses and recoveries. Next bank partners that settle redemptions in fiat on regulated rails. Then third party attestation of Shariah processes by a well known standards body. Finally clear tax treatment for token holders in local law.
Open questions to track
How quickly can issuers update allow lists without friction. How will secondary liquidity work if most buyers hold to maturity. What level of disclosure will investors expect at the pool level. Answers to these questions will shape adoption.

