
Executive brief
Kraken completed a full migration of its Ethereum validators to Distributed Validator Technology (DVT) using SSV Network. The goal is higher availability, lower slashing risk, and multi‑client resilience at institutional scale.
DVT in one paragraph
DVT splits a validator key into key shares and requires threshold signatures across a cluster of independent nodes that act as a single logical validator. If a node fails or is under maintenance, the validator remains live. Clusters can mix clients, hardware and geographies, which reduces single points of failure.
Why this matters
Uptime: maintenance and localized failures have less impact on participation.
Risk: lower probability of correlated slashing events.
Client diversity: better mix of consensus and execution clients.
Institutional signal: DVT has moved from pilots to production at a top exchange.
Relative operating risks for validators: Traditional vs DVT (illustrative)
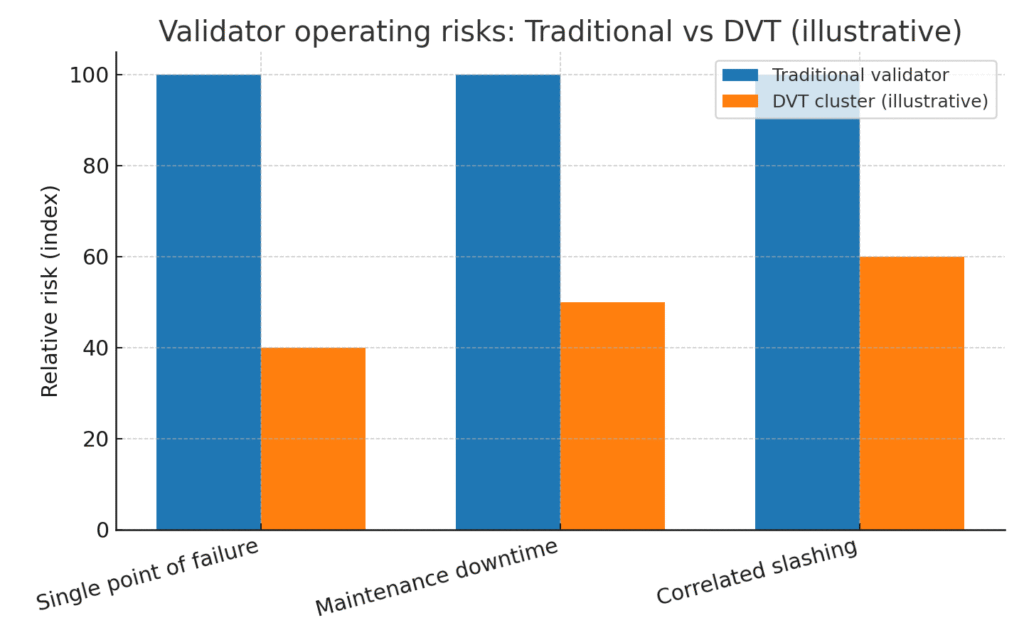
Validator operating risks: Traditional vs DVT (illustrative index)
Quick comparison of DVT options
DVT options for Ethereum validators: operating model, adoption and trade offs
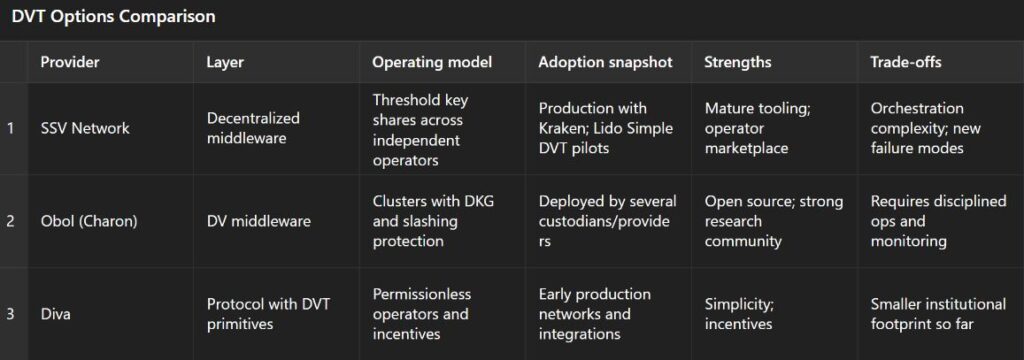
Notes: Adoption snapshot is indicative based on public information and industry reporting.
What changed at Kraken
All ETH validators now operate in DVT clusters.
Multi client architecture with coordinated slashing protection.
Objective: institutional grade reliability and performance for staking customers.
Mini interview
Q: Why run DVT in production now
A: Uptime and maintenance flexibility are the big wins. Threshold signing and independent operators reduce correlated risks.
Q: Main operational challenge
A: Observability and automation. The benefits compound when you standardize deployment, alerts and runbooks.
Q: What changes for end users
A: A more stable effective APR and fewer penalties due to outages.
Signals to monitor
Kraken validator participation before and after DVT.
Public slashing statistics for DVT operators.
Mix of clients and geographies inside clusters.
Adoption of DVT by other custodians and liquid staking protocols.
Institutional checklist
Map operational ownership and SLAs across operators.
Hardening of key share custody and rotation.
Unified logging and metrics with clear SLOs.
Periodic chaos tests to validate failover and quorum thresholds.

